这篇文章主要围绕重写Oauth2生成access_token,实现踢下线功能和oauth2access_token展开,旨在为您提供一份详细的参考资料。我们将全面介绍重写Oauth2生成access_
这篇文章主要围绕重写Oauth2生成access_token,实现踢下线功能和oauth2 access_token展开,旨在为您提供一份详细的参考资料。我们将全面介绍重写Oauth2生成access_token,实现踢下线功能的优缺点,解答oauth2 access_token的相关问题,同时也会为您带来.NET 请求认证之access-token(oauth2.0与owin的结合)、android-OAuth2请求缺少参数access_token、easywehat插件在初始化时会生成access_token,如果多台机器使用access_token,需要自定义设置access_token、firebase oauth2 accessToken 没用的实用方法。
本文目录一览:- 重写Oauth2生成access_token,实现踢下线功能(oauth2 access_token)
- .NET 请求认证之access-token(oauth2.0与owin的结合)
- android-OAuth2请求缺少参数access_token
- easywehat插件在初始化时会生成access_token,如果多台机器使用access_token,需要自定义设置access_token
- firebase oauth2 accessToken 没用

重写Oauth2生成access_token,实现踢下线功能(oauth2 access_token)
根据项目的特殊需求,需要实现账号在另一端登录时,踢掉该账号在其他端登录的功能
查看源码发现oauth2默认的生成access_token不能达到预期效果.
源码DefaultTokenServices :
package org.springframework.security.oauth2.provider.token;
import ...
public class DefaultTokenServices implements AuthorizationServerTokenServices, ResourceServerTokenServices,
ConsumerTokenServices, InitializingBean {
private int refreshTokenValiditySeconds = 60 * 60 * 24 * 30; // default 30 days.
private int accessTokenValiditySeconds = 60 * 60 * 12; // default 12 hours.
private boolean supportRefreshToken = false;
private boolean reuseRefreshToken = true;
private TokenStore tokenStore;
private ClientDetailsService clientDetailsService;
private TokenEnhancer accessTokenEnhancer;
private AuthenticationManager authenticationManager;
/**
* Initialize these token services. If no random generator is set, one will be created.
*/
public void afterPropertiesSet() throws Exception {
Assert.notNull(tokenStore, "tokenStore must be set");
}
@Transactional
public OAuth2AccessToken createAccessToken(OAuth2Authentication authentication) throws AuthenticationException {
OAuth2AccessToken existingAccessToken = tokenStore.getAccessToken(authentication);
OAuth2RefreshToken refreshToken = null;
if (existingAccessToken != null) {
if (existingAccessToken.isExpired()) {
if (existingAccessToken.getRefreshToken() != null) {
refreshToken = existingAccessToken.getRefreshToken();
// The token store could remove the refresh token when the
// access token is removed, but we want to
// be sure...
tokenStore.removeRefreshToken(refreshToken);
}
tokenStore.removeAccessToken(existingAccessToken);
}
else {
// Re-store the access token in case the authentication has changed
tokenStore.storeAccessToken(existingAccessToken, authentication);
return existingAccessToken;
}
}
// Only create a new refresh token if there wasn''t an existing one
// associated with an expired access token.
// Clients might be holding existing refresh tokens, so we re-use it in
// the case that the old access token
// expired.
if (refreshToken == null) {
refreshToken = createRefreshToken(authentication);
}
// But the refresh token itself might need to be re-issued if it has
// expired.
else if (refreshToken instanceof ExpiringOAuth2RefreshToken) {
ExpiringOAuth2RefreshToken expiring = (ExpiringOAuth2RefreshToken) refreshToken;
if (System.currentTimeMillis() > expiring.getExpiration().getTime()) {
refreshToken = createRefreshToken(authentication);
}
}
OAuth2AccessToken accessToken = createAccessToken(authentication, refreshToken);
tokenStore.storeAccessToken(accessToken, authentication);
// In case it was modified
refreshToken = accessToken.getRefreshToken();
if (refreshToken != null) {
tokenStore.storeRefreshToken(refreshToken, authentication);
}
return accessToken;
}
@Transactional(noRollbackFor={InvalidTokenException.class, InvalidGrantException.class})
public OAuth2AccessToken refreshAccessToken(String refreshTokenValue, TokenRequest tokenRequest)
throws AuthenticationException {
if (!supportRefreshToken) {
throw new InvalidGrantException("Invalid refresh token: " + refreshTokenValue);
}
OAuth2RefreshToken refreshToken = tokenStore.readRefreshToken(refreshTokenValue);
if (refreshToken == null) {
throw new InvalidGrantException("Invalid refresh token: " + refreshTokenValue);
}
OAuth2Authentication authentication = tokenStore.readAuthenticationForRefreshToken(refreshToken);
if (this.authenticationManager != null && !authentication.isClientOnly()) {
// The client has already been authenticated, but the user authentication might be old now, so give it a
// chance to re-authenticate.
Authentication user = new PreAuthenticatedAuthenticationToken(authentication.getUserAuthentication(), "", authentication.getAuthorities());
user = authenticationManager.authenticate(user);
Object details = authentication.getDetails();
authentication = new OAuth2Authentication(authentication.getOAuth2Request(), user);
authentication.setDetails(details);
}
String clientId = authentication.getOAuth2Request().getClientId();
if (clientId == null || !clientId.equals(tokenRequest.getClientId())) {
throw new InvalidGrantException("Wrong client for this refresh token: " + refreshTokenValue);
}
// clear out any access tokens already associated with the refresh
// token.
tokenStore.removeAccessTokenUsingRefreshToken(refreshToken);
if (isExpired(refreshToken)) {
tokenStore.removeRefreshToken(refreshToken);
throw new InvalidTokenException("Invalid refresh token (expired): " + refreshToken);
}
authentication = createRefreshedAuthentication(authentication, tokenRequest);
if (!reuseRefreshToken) {
tokenStore.removeRefreshToken(refreshToken);
refreshToken = createRefreshToken(authentication);
}
OAuth2AccessToken accessToken = createAccessToken(authentication, refreshToken);
tokenStore.storeAccessToken(accessToken, authentication);
if (!reuseRefreshToken) {
tokenStore.storeRefreshToken(accessToken.getRefreshToken(), authentication);
}
return accessToken;
}
public OAuth2AccessToken getAccessToken(OAuth2Authentication authentication) {
return tokenStore.getAccessToken(authentication);
}
/**
* Create a refreshed authentication.
*
* @param authentication The authentication.
* @param request The scope for the refreshed token.
* @return The refreshed authentication.
* @throws InvalidScopeException If the scope requested is invalid or wider than the original scope.
*/
private OAuth2Authentication createRefreshedAuthentication(OAuth2Authentication authentication, TokenRequest request) {
OAuth2Authentication narrowed = authentication;
Set<String> scope = request.getScope();
OAuth2Request clientAuth = authentication.getOAuth2Request().refresh(request);
if (scope != null && !scope.isEmpty()) {
Set<String> originalScope = clientAuth.getScope();
if (originalScope == null || !originalScope.containsAll(scope)) {
throw new InvalidScopeException("Unable to narrow the scope of the client authentication to " + scope
+ ".", originalScope);
}
else {
clientAuth = clientAuth.narrowScope(scope);
}
}
narrowed = new OAuth2Authentication(clientAuth, authentication.getUserAuthentication());
return narrowed;
}
protected boolean isExpired(OAuth2RefreshToken refreshToken) {
if (refreshToken instanceof ExpiringOAuth2RefreshToken) {
ExpiringOAuth2RefreshToken expiringToken = (ExpiringOAuth2RefreshToken) refreshToken;
return expiringToken.getExpiration() == null
|| System.currentTimeMillis() > expiringToken.getExpiration().getTime();
}
return false;
}
public OAuth2AccessToken readAccessToken(String accessToken) {
return tokenStore.readAccessToken(accessToken);
}
public OAuth2Authentication loadAuthentication(String accessTokenValue) throws AuthenticationException,
InvalidTokenException {
OAuth2AccessToken accessToken = tokenStore.readAccessToken(accessTokenValue);
if (accessToken == null) {
throw new InvalidTokenException("Invalid access token: " + accessTokenValue);
}
else if (accessToken.isExpired()) {
tokenStore.removeAccessToken(accessToken);
throw new InvalidTokenException("Access token expired: " + accessTokenValue);
}
OAuth2Authentication result = tokenStore.readAuthentication(accessToken);
if (result == null) {
// in case of race condition
throw new InvalidTokenException("Invalid access token: " + accessTokenValue);
}
if (clientDetailsService != null) {
String clientId = result.getOAuth2Request().getClientId();
try {
clientDetailsService.loadClientByClientId(clientId);
}
catch (ClientRegistrationException e) {
throw new InvalidTokenException("Client not valid: " + clientId, e);
}
}
return result;
}
public String getClientId(String tokenValue) {
OAuth2Authentication authentication = tokenStore.readAuthentication(tokenValue);
if (authentication == null) {
throw new InvalidTokenException("Invalid access token: " + tokenValue);
}
OAuth2Request clientAuth = authentication.getOAuth2Request();
if (clientAuth == null) {
throw new InvalidTokenException("Invalid access token (no client id): " + tokenValue);
}
return clientAuth.getClientId();
}
public boolean revokeToken(String tokenValue) {
OAuth2AccessToken accessToken = tokenStore.readAccessToken(tokenValue);
if (accessToken == null) {
return false;
}
if (accessToken.getRefreshToken() != null) {
tokenStore.removeRefreshToken(accessToken.getRefreshToken());
}
tokenStore.removeAccessToken(accessToken);
return true;
}
private OAuth2RefreshToken createRefreshToken(OAuth2Authentication authentication) {
if (!isSupportRefreshToken(authentication.getOAuth2Request())) {
return null;
}
int validitySeconds = getRefreshTokenValiditySeconds(authentication.getOAuth2Request());
String value = UUID.randomUUID().toString();
if (validitySeconds > 0) {
return new DefaultExpiringOAuth2RefreshToken(value, new Date(System.currentTimeMillis()
+ (validitySeconds * 1000L)));
}
return new DefaultOAuth2RefreshToken(value);
}
private OAuth2AccessToken createAccessToken(OAuth2Authentication authentication, OAuth2RefreshToken refreshToken) {
DefaultOAuth2AccessToken token = new DefaultOAuth2AccessToken(UUID.randomUUID().toString());
int validitySeconds = getAccessTokenValiditySeconds(authentication.getOAuth2Request());
if (validitySeconds > 0) {
token.setExpiration(new Date(System.currentTimeMillis() + (validitySeconds * 1000L)));
}
token.setRefreshToken(refreshToken);
token.setScope(authentication.getOAuth2Request().getScope());
return accessTokenEnhancer != null ? accessTokenEnhancer.enhance(token, authentication) : token;
}
/**
* The access token validity period in seconds
*
* @param clientAuth the current authorization request
* @return the access token validity period in seconds
*/
protected int getAccessTokenValiditySeconds(OAuth2Request clientAuth) {
if (clientDetailsService != null) {
ClientDetails client = clientDetailsService.loadClientByClientId(clientAuth.getClientId());
Integer validity = client.getAccessTokenValiditySeconds();
if (validity != null) {
return validity;
}
}
return accessTokenValiditySeconds;
}
/**
* The refresh token validity period in seconds
*
* @param clientAuth the current authorization request
* @return the refresh token validity period in seconds
*/
protected int getRefreshTokenValiditySeconds(OAuth2Request clientAuth) {
if (clientDetailsService != null) {
ClientDetails client = clientDetailsService.loadClientByClientId(clientAuth.getClientId());
Integer validity = client.getRefreshTokenValiditySeconds();
if (validity != null) {
return validity;
}
}
return refreshTokenValiditySeconds;
}
/**
* Is a refresh token supported for this client (or the global setting if
* {@link #setClientDetailsService(ClientDetailsService) clientDetailsService} is not set.
*
* @param clientAuth the current authorization request
* @return boolean to indicate if refresh token is supported
*/
protected boolean isSupportRefreshToken(OAuth2Request clientAuth) {
if (clientDetailsService != null) {
ClientDetails client = clientDetailsService.loadClientByClientId(clientAuth.getClientId());
return client.getAuthorizedGrantTypes().contains("refresh_token");
}
return this.supportRefreshToken;
}
/**
* An access token enhancer that will be applied to a new token before it is saved in the token store.
*
* @param accessTokenEnhancer the access token enhancer to set
*/
public void setTokenEnhancer(TokenEnhancer accessTokenEnhancer) {
this.accessTokenEnhancer = accessTokenEnhancer;
}
/**
* The validity (in seconds) of the refresh token. If less than or equal to zero then the tokens will be
* non-expiring.
*
* @param refreshTokenValiditySeconds The validity (in seconds) of the refresh token.
*/
public void setRefreshTokenValiditySeconds(int refreshTokenValiditySeconds) {
this.refreshTokenValiditySeconds = refreshTokenValiditySeconds;
}
/**
* The default validity (in seconds) of the access token. Zero or negative for non-expiring tokens. If a client
* details service is set the validity period will be read from the client, defaulting to this value if not defined
* by the client.
*
* @param accessTokenValiditySeconds The validity (in seconds) of the access token.
*/
public void setAccessTokenValiditySeconds(int accessTokenValiditySeconds) {
this.accessTokenValiditySeconds = accessTokenValiditySeconds;
}
/**
* Whether to support the refresh token.
*
* @param supportRefreshToken Whether to support the refresh token.
*/
public void setSupportRefreshToken(boolean supportRefreshToken) {
this.supportRefreshToken = supportRefreshToken;
}
/**
* Whether to reuse refresh tokens (until expired).
*
* @param reuseRefreshToken Whether to reuse refresh tokens (until expired).
*/
public void setReuseRefreshToken(boolean reuseRefreshToken) {
this.reuseRefreshToken = reuseRefreshToken;
}
/**
* The persistence strategy for token storage.
*
* @param tokenStore the store for access and refresh tokens.
*/
public void setTokenStore(TokenStore tokenStore) {
this.tokenStore = tokenStore;
}
/**
* An authentication manager that will be used (if provided) to check the user authentication when a token is
* refreshed.
*
* @param authenticationManager the authenticationManager to set
*/
public void setAuthenticationManager(AuthenticationManager authenticationManager) {
this.authenticationManager = authenticationManager;
}
/**
* The client details service to use for looking up clients (if necessary). Optional if the access token expiry is
* set globally via {@link #setAccessTokenValiditySeconds(int)}.
*
* @param clientDetailsService the client details service
*/
public void setClientDetailsService(ClientDetailsService clientDetailsService) {
this.clientDetailsService = clientDetailsService;
}
}关键点源码:
@Transactional
public OAuth2AccessToken createAccessToken(OAuth2Authentication authentication) throws AuthenticationException {
OAuth2AccessToken existingAccessToken = this.tokenStore.getAccessToken(authentication);
OAuth2RefreshToken refreshToken = null;
if (existingAccessToken != null) {
if (!existingAccessToken.isExpired()) {
this.tokenStore.storeAccessToken(existingAccessToken, authentication);
return existingAccessToken;
}
if (existingAccessToken.getRefreshToken() != null) {
refreshToken = existingAccessToken.getRefreshToken();
this.tokenStore.removeRefreshToken(refreshToken);
}
this.tokenStore.removeAccessToken(existingAccessToken);
}
if (refreshToken == null) {
refreshToken = this.createRefreshToken(authentication);
} else if (refreshToken instanceof ExpiringOAuth2RefreshToken) {
ExpiringOAuth2RefreshToken expiring = (ExpiringOAuth2RefreshToken)refreshToken;
if (System.currentTimeMillis() > expiring.getExpiration().getTime()) {
refreshToken = this.createRefreshToken(authentication);
}
}
OAuth2AccessToken accessToken = this.createAccessToken(authentication, refreshToken);
this.tokenStore.storeAccessToken(accessToken, authentication);
refreshToken = accessToken.getRefreshToken();
if (refreshToken != null) {
this.tokenStore.storeRefreshToken(refreshToken, authentication);
}
return accessToken;
}实现踢下线功能需要修改此处!
实现的内容:
新建一个class并且extends defaultTokenServices
如下:
/**
* 重写oauth2 生成accesstoken
* @author LIUBAO
* @date 2020/12/2 15:50
*/
public class CustomDefaultTokenServices extends DefaultTokenServices {
private TokenStore tokenStore;
private TokenEnhancer accessTokenEnhancer;
public CustomDefaultTokenServices() {
}
public CustomDefaultTokenServices(TokenStore tokenStore,TokenEnhancer accessTokenEnhancer){
super.setTokenStore(tokenStore);
this.tokenStore = tokenStore;
this.accessTokenEnhancer = accessTokenEnhancer;
}
@Override
@Transactional
public OAuth2AccessToken createAccessToken(OAuth2Authentication authentication) throws AuthenticationException {
OAuth2AccessToken existingAccessToken = this.tokenStore.getAccessToken(authentication);
OAuth2RefreshToken refreshToken = null;
if (existingAccessToken != null) {
if (existingAccessToken.getRefreshToken() != null) {
//去掉判断直接删除
refreshToken = existingAccessToken.getRefreshToken();
// The token store could remove the refresh token when the
// access token is removed, but we want to
// be sure...
this.tokenStore.removeRefreshToken(refreshToken);
}
this.tokenStore.removeAccessToken(existingAccessToken);
}
// Only create a new refresh token if there wasn''t an existing one
// associated with an expired access token.
// Clients might be holding existing refresh tokens, so we re-use it in
// the case that the old access token
// expired.
if (refreshToken == null) {
refreshToken = createRefreshToken(authentication);
}
// But the refresh token itself might need to be re-issued if it has
// expired.
else if (refreshToken instanceof ExpiringOAuth2RefreshToken) {
ExpiringOAuth2RefreshToken expiring = (ExpiringOAuth2RefreshToken) refreshToken;
if (System.currentTimeMillis() > expiring.getExpiration().getTime()) {
refreshToken = createRefreshToken(authentication);
}
}
OAuth2AccessToken accessToken = createAccessToken(authentication, refreshToken);
this.tokenStore.storeAccessToken(accessToken, authentication);
// In case it was modified
refreshToken = accessToken.getRefreshToken();
if (refreshToken != null) {
this.tokenStore.storeRefreshToken(refreshToken, authentication);
}
return accessToken;
}
private OAuth2RefreshToken createRefreshToken(OAuth2Authentication authentication) {
if (!this.isSupportRefreshToken(authentication.getOAuth2Request())) {
return null;
} else {
int validitySeconds = this.getRefreshTokenValiditySeconds(authentication.getOAuth2Request());
String value = UUID.randomUUID().toString();
return (OAuth2RefreshToken)(validitySeconds > 0 ? new DefaultExpiringOAuth2RefreshToken(value, new Date(System.currentTimeMillis() + (long)validitySeconds * 1000L)) : new DefaultOAuth2RefreshToken(value));
}
}
private OAuth2AccessToken createAccessToken(OAuth2Authentication authentication, OAuth2RefreshToken refreshToken) {
DefaultOAuth2AccessToken token = new DefaultOAuth2AccessToken(UUID.randomUUID().toString());
int validitySeconds = this.getAccessTokenValiditySeconds(authentication.getOAuth2Request());
if (validitySeconds > 0) {
token.setExpiration(new Date(System.currentTimeMillis() + (long)validitySeconds * 1000L));
}
token.setRefreshToken(refreshToken);
token.setScope(authentication.getOAuth2Request().getScope());
return (OAuth2AccessToken)(this.accessTokenEnhancer != null ? this.accessTokenEnhancer.enhance(token, authentication) : token);
}
}
然后在AuthorizationServerConfig里面配置就行了


.NET 请求认证之access-token(oauth2.0与owin的结合)
公司对外开放的接口,大多需要请求认证,如微信,阿里等。最近我刚好在搭建webapi框架。记录一下自己的理解。
一:请求认证的目的
之所以要对我们的接口进行请求认证,就是为了安全考虑的。以前都是在用别人给我的规则去生成token,现在也轮到自己开发了。嘿嘿
二:开发思路
1:请求接口之前,用户必须先去请求获得我们的access-token。每次请求必须得带上access-token来请求我的接口。否则我们会拒绝外部请求。
2:access-token有时间的限制,过期的请求我们依然会拒绝。
3:对不同的外部者,应有不同的clientID。以便分配不同的权限。以后不合作了,我们可以取消他们的认证,并不会影响其他的客户。类似于微信的 Appid,Appsecret
三:创建Access-Token
在api项目里token验证发生在进入接口之前,需要有一个启动文件来执行token的判断。在API项目下创建Startup.cs类。
我们需要在Nuget引用以下DLL:
- Microsoft.Owin.Security.OAuth
- Microsoft.Owin.Security
- Microsoft.Owin
- Microsoft.Owin.Host.SystemWeb
- OWIN
- Microsoft ASP.Net Web API 2.2 OWIN
- Microsoft ASP.Net Identity OWIN
using System;
using System.Collections.Generic;
using System.Linq;
using System.Web.Http;
using Bn.Common;
using Microsoft.Owin;
using Microsoft.Owin.Cors;
using Microsoft.Owin.Security;
using Microsoft.Owin.Security.OAuth;
using Owin;
[assembly: OwinStartup(typeof(BnWebApi.Startup))]
namespace BnWebApi
{
/// <summary>
/// wuchen19-4-15
/// </summary>
public partial class Startup
{
//public void Configuration(IAppBuilder app)
//{
// ConfigureAuth(app);
//}
public void Configuration(IAppBuilder app)
{
HttpConfiguration config = new HttpConfiguration();
WebApiConfig.Register(config);
ConfigureOAuth(app);
app.UseCors(CorsOptions.AllowAll);
app.UseWebApi(config);
}
public void ConfigureOAuth(IAppBuilder app)
{
var OAuthServerOptions = new OAuthAuthorizationServerOptions()
{
AllowInsecureHttp = true, //允许客户端使用Http协议请求
TokenEndpointPath = new PathString("/token"), //请求地址
//AccessTokenExpireTimeSpan = TimeSpan.FromDays(1), //token过期时间
AccessTokenExpireTimeSpan = TimeSpan.FromHours(1),
Provider = new SimpleAuthorizationServerProvider(),//提供认证策略
RefreshTokenProvider = new SimpleRefreshTokenProvider() //refresh_token 授权服务
};
app.UseOAuthAuthorizationServer(OAuthServerOptions);
app.UseOAuthBearerAuthentication(new OAuthBearerAuthenticationOptions());
}
}
}这个SimpleRefreshTokenProvider()方法就是我们验证Client信息和生成Token的地方
using System;
using System.Collections.Generic;
using System.Linq;
using System.Security.Claims;
using System.Text;
using System.Threading.Tasks;
using Microsoft.Owin.Security;
using Microsoft.Owin.Security.OAuth;
using System.Configuration;
namespace Bn.Common
{
/// <summary>
/// Token验证 wuchen 5-17
/// </summary>
public class SimpleAuthorizationServerProvider : OAuthAuthorizationServerProvider
{
#region AccessToken生成机制 密码模式
////Oauth AccessToken grant_type=password
//public override async Task ValidateClientAuthentication(OAuthValidateClientAuthenticationContext context)
//{
// await Task.Factory.StartNew(() => context.Validated());
//}
//public override async Task GrantResourceOwnerCredentials(OAuthGrantResourceOwnerCredentialsContext context)
//{
// await Task.Factory.StartNew(() => context.OwinContext.Response.Headers.Add("Access-Control-Allow-Origin", new[] { "*" }));
// var identity = new ClaimsIdentity(context.Options.AuthenticationType);
// var bnauth = ConfigurationManager.AppSettings["Oauth"]; //BnUser-123456
// var bnstr = bnauth.Split(''-'');
// var bnuser = bnstr[0];
// var bnpassword = bnstr[1];
// if (context.UserName != bnuser || context.Password != bnpassword)
// {
// context.SetError("invalid_client", "账号密码认证失败");
// return;
// }
// identity.AddClaim(new Claim("sub", context.UserName));
// identity.AddClaim(new Claim("role", "user"));
// context.Validated(identity);
//}
#endregion
#region AccessToken生成机制 客户端模式
// grant_type= client_credentials
public override async Task ValidateClientAuthentication(OAuthValidateClientAuthenticationContext context)
{
string clientId;
string clientSecret;
context.TryGetFormCredentials(out clientId, out clientSecret);
//验证
//var bnauth = ConfigurationManager.AppSettings["Oauth"]; //BnUser-123456
//var bnstr = bnauth.Split(''-'');
//var bnuser = bnstr[0];
//var bnpassword = bnstr[1];
//if (clientId != bnuser || clientSecret != bnpassword)
//{
// context.SetError("invalid_client", "账号密码认证失败");
// return;
//}
var gkey = ConfigurationManager.AppSettings[clientId]; //BnUser-123456
if (clientSecret != gkey)
{
context.SetError("invalid_client", "账号密码认证失败");
return;
}
context.OwinContext.Set("as:client_id", clientId);
await Task.Factory.StartNew(() => context.Validated(clientId));
//context.Validated(clientId);
}
/// <summary>
/// 客户端授权[生成access token]
/// </summary>
/// <param name="context"></param>
/// <returns></returns>
public override Task GrantClientCredentials(OAuthGrantClientCredentialsContext context)
{
var oAuthIdentity = new ClaimsIdentity(context.Options.AuthenticationType);
oAuthIdentity.AddClaim(new Claim(ClaimTypes.Name, context.OwinContext.Get<string>("as:client_id")));
var ticket = new AuthenticationTicket(oAuthIdentity, new AuthenticationProperties { AllowRefresh = true });
context.Validated(ticket);
return base.GrantClientCredentials(context);
}
#endregion
}
}两种模式都是可以用的。。密码模式和客户端模式。GrantClientCredentials方法为我们生成Token的方法。。有了这些我们就可以生成token啦。
Oauth支持的5类 grant_type 及说明(
authorization_code — 授权码模式(即先登录获取code,再获取token)
password — 密码模式(将用户名,密码传过去,直接获取token)
client_credentials — 客户端模式(无用户,用户向客户端注册,然后客户端以自己的名义向’服务端’获取资源)
implicit — 简化模式(在redirect_uri 的Hash传递token; Auth客户端运行在浏览器中,如JS,Flash)
refresh_token — 刷新access_token)
四:获取Token
输入参数:grant_type:验证模式 , client_id :服务端定义 , client_secret:秘钥 服务端和客户端共同保存 类似于微信的Appsecrret
生成项目,然后本地用Postman调试

返回的参数分别是:access_token:我们需要的token token_type :bearer (协议固定) expires_in:有效期(可以自定义) refresh_token:token重新过期后,重新获取token用到(暂时没用)
五:使用access_token访问接口路由
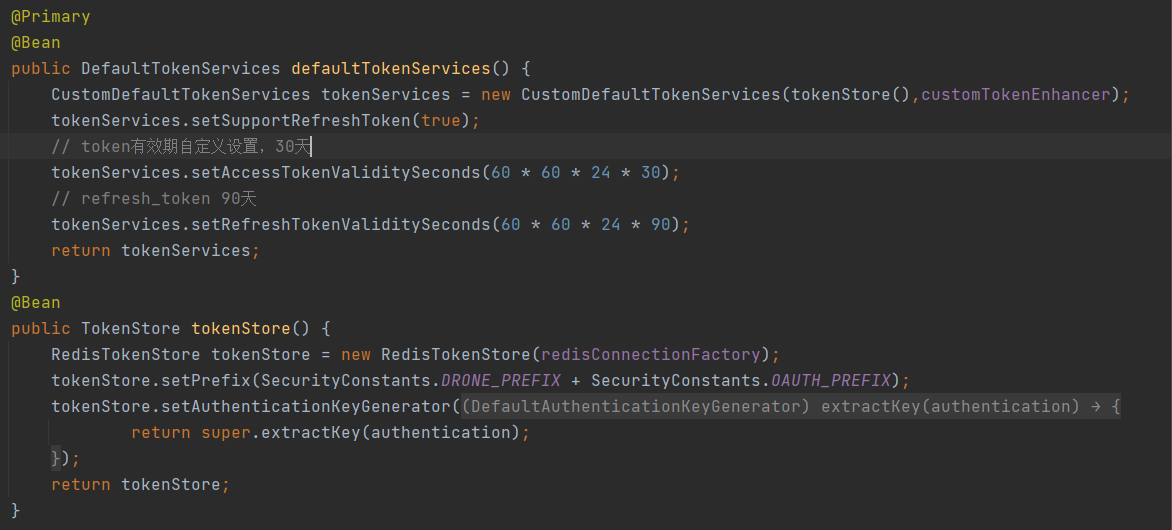
在Webapi中 ,我们用在方法加上 Authorize ,来表示这个方法访问需要授权, 如果不加Authorize ,那么token就没有意义。。 如下
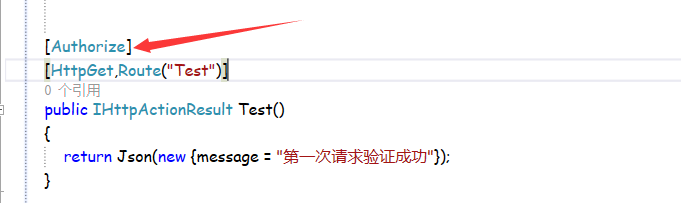
我们不带token访问一下看看:
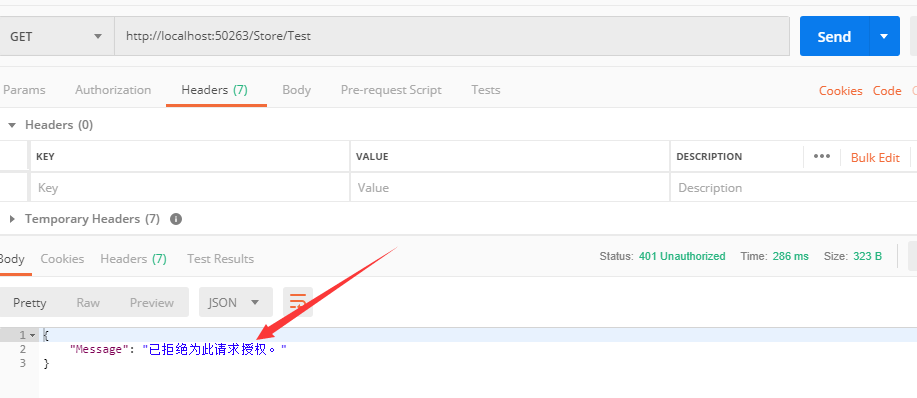
显示已拒绝我们的请求授权。
加了access-Token之后,注意token放的位置,在请求头Headers里 添加 Authorization:bearer token。 bearer与token之间有一个空格
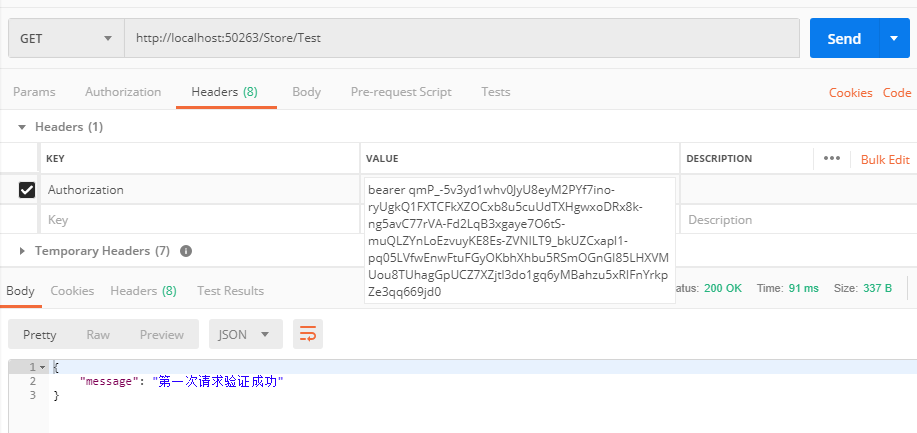
验证的过程,是在我们Oauth2.0封装起来啦,可以查看。
到这里,用Oauth2.0加Owin的Webapi请求验证--accesstoken完成。。基本每一步都有注释,很好理解
简单的两句代码,双倍的快乐

android-OAuth2请求缺少参数access_token
我正在使用Apache Amber库尝试在我的控制下从网站检索OAuth2访问令牌.我的客户端代码在Android下运行.
我的代码以示例为例:
https://cwiki.apache.org/confluence/display/AMBER/OAuth+2.0+Client+Quickstart
第一步,我可以通过使用WebView浏览器提交GET请求来检索“代码”:
OAuthClientRequest request = OAuthClientRequest
.authorizationLocation(AUTHORIZE_URL)
.setClientId(CLIENT_ID)
.setRedirectURI(REDIR_URL)
.setResponseType(CODE_RESPONSE)
.buildQueryMessage();
webview.loadUrl(request.getLocationUri());
我使用WebViewClient回调来捕获带有“ code”参数的重定向URL.到现在为止还挺好.
使用该代码,我尝试检索访问令牌:
OAuthClient oAuthClient = new OAuthClient(new URLConnectionClient());
OAuthClientRequest request = OAuthClientRequest
.tokenLocation(ACCESS_TOKEN_URL)
.setGrantType(GrantType.AUTHORIZATION_CODE)
.setClientId(CLIENT_ID)
.setClientSecret(CLIENT_SECRET)
.setRedirectURI(REDIR_URL)
.setCode(code)
.buildBodyMessage();
GitHubTokenResponse oAuthResponse =
oAuthClient.accesstoken(request, GitHubTokenResponse.class);
每次运行代码时,我都会收到OAuthProblemException,该消息是由于缺少参数access_token而导致我的请求无效.
另一个StackOverflow帖子提到了来自类似OAuth2请求的此异常,在这种情况下,该异常是由OAuth请求中的不同重定向URI引起的.但是我通过使用命名常量来确保重定向URI相同.这是该帖子的链接:
OAuthProblem, missing parameter access_token
现在,我可以打印出第一个请求返回的代码,并将其粘贴到从我的台式机运行的curl命令中:
curl -d“代码= …& client_id = …& client_secret = …& grant_type = …& redirect_uri = …” http://my_website.com
并且我从我的网站上获得了一个带有access_token的不错的JSON响应.
为什么从Java的调用失败,而我手动滚动的命令行成功了?
解决方法:
我在实现客户端和服务器时遇到了相同的问题,该问题与Apache Amber(Oltu)项目中的Client Example中的一个错误有关:
首先,您有Auth代码请求(有效):
OAuthClientRequest request = OAuthClientRequest
.authorizationLocation(AUTHORIZE_URL)
.setClientId(CLIENT_ID)
.setRedirectURI(REDIR_URL)
.setResponseType(CODE_RESPONSE)
.**buildQueryMessage**();
其次是关于访问令牌的请求(无效):
OAuthClientRequest request = OAuthClientRequest
.tokenLocation(ACCESS_TOKEN_URL)
.setGrantType(GrantType.AUTHORIZATION_CODE)
.setClientId(CLIENT_ID)
.setClientSecret(CLIENT_SECRET)
.setRedirectURI(REDIR_URL)
.setCode(code)
.**buildBodyMessage**();
错误与第二个请求中的buildBodyMessage()有关.通过buildQueryMessage()对其进行更改.

easywehat插件在初始化时会生成access_token,如果多台机器使用access_token,需要自定义设置access_token
easywehat插件在初始化时会生成access_token,如果多台机器使用access_token,需要自定义设置access_token
比如有两个项目都用了同一个小程序,那么一个项目生成access_token会造成另一个项目的access_token失效报错
firebase oauth2 accessToken 没用
如何解决firebase oauth2 accessToken 没用?
在 firebase 中,我们可以使用 signInWithPopup 并通过 credential.accesstoken 获取我们的身份验证提供程序访问令牌。
我们只能在登录后获得一次这个 accesstoken。但是这个访问令牌在一小时内过期!
我们需要强制用户再次登录以获取访问令牌。
这种完全无用的访问令牌用户体验有何意义?如果我们无论如何都不能使用它。
更新:
我正在使用 Firebase 开发 Chrome 扩展程序并尝试添加 Google 日历支持。我已经花了几天但没有找到解决方案。
首先 GAPI 在 Chrome 扩展中不起作用。我尝试使用 signInWithPopup 并通过 REST 调用来实现,但 firebase 中的 google.com oauth2 访问令牌在一小时后到期,并且无法静默刷新它。
这就是 Google 的所有产品,为什么它们很难协同工作?
更新 2:
provider = new firebase.auth.GoogleAuthProvider();
provider.addScope(''https://www.googleapis.com/auth/calendar.events'');
const result = await firebase.auth().signInWithPopup(provider)
var credential = result.credential;
// Saving **credential** somewhere for later use it in REST calls to` https://www.googleapis.com/calendar/v3/users/me/calendarList
问题此访问令牌在一小时后过期。
解决方法
暂无找到可以解决该程序问题的有效方法,小编努力寻找整理中!
如果你已经找到好的解决方法,欢迎将解决方案带上本链接一起发送给小编。
小编邮箱:dio#foxmail.com (将#修改为@)
今天关于重写Oauth2生成access_token,实现踢下线功能和oauth2 access_token的分享就到这里,希望大家有所收获,若想了解更多关于.NET 请求认证之access-token(oauth2.0与owin的结合)、android-OAuth2请求缺少参数access_token、easywehat插件在初始化时会生成access_token,如果多台机器使用access_token,需要自定义设置access_token、firebase oauth2 accessToken 没用等相关知识,可以在本站进行查询。
本文标签:



![[转帖]Ubuntu 安装 Wine方法(ubuntu如何安装wine)](https://www.gvkun.com/zb_users/cache/thumbs/4c83df0e2303284d68480d1b1378581d-180-120-1.jpg)

